Malicious cyber activity has seen a steep increase within the past two years. With organizations forced to support remote work, many threat actors are taking advantage of weaknesses in these hastily prepared resources. Many more are enticed by the success these criminals have had. To date, ProviderSoft is proud to say we have successfully defended the data of our Clients and our internal systems.
At ProviderSoft, we take the protection of our networks and your data very seriously. With this increase in malicious activity, we have further bolstered this protection and will continue to do so. Please see below for more information on security risks and an overview of the protective measures this increase will help support.
Between 2019 and 2020, the number of ransomware attacks have almost doubled (FireEye)
An astounding 88% of organizations worldwide experienced phishing attempts in 2019 (Proofpoint). Data breaches, including those that were healthcare adjacent, exposed 36 billion records in only the first half of 2020 (RiskBased).
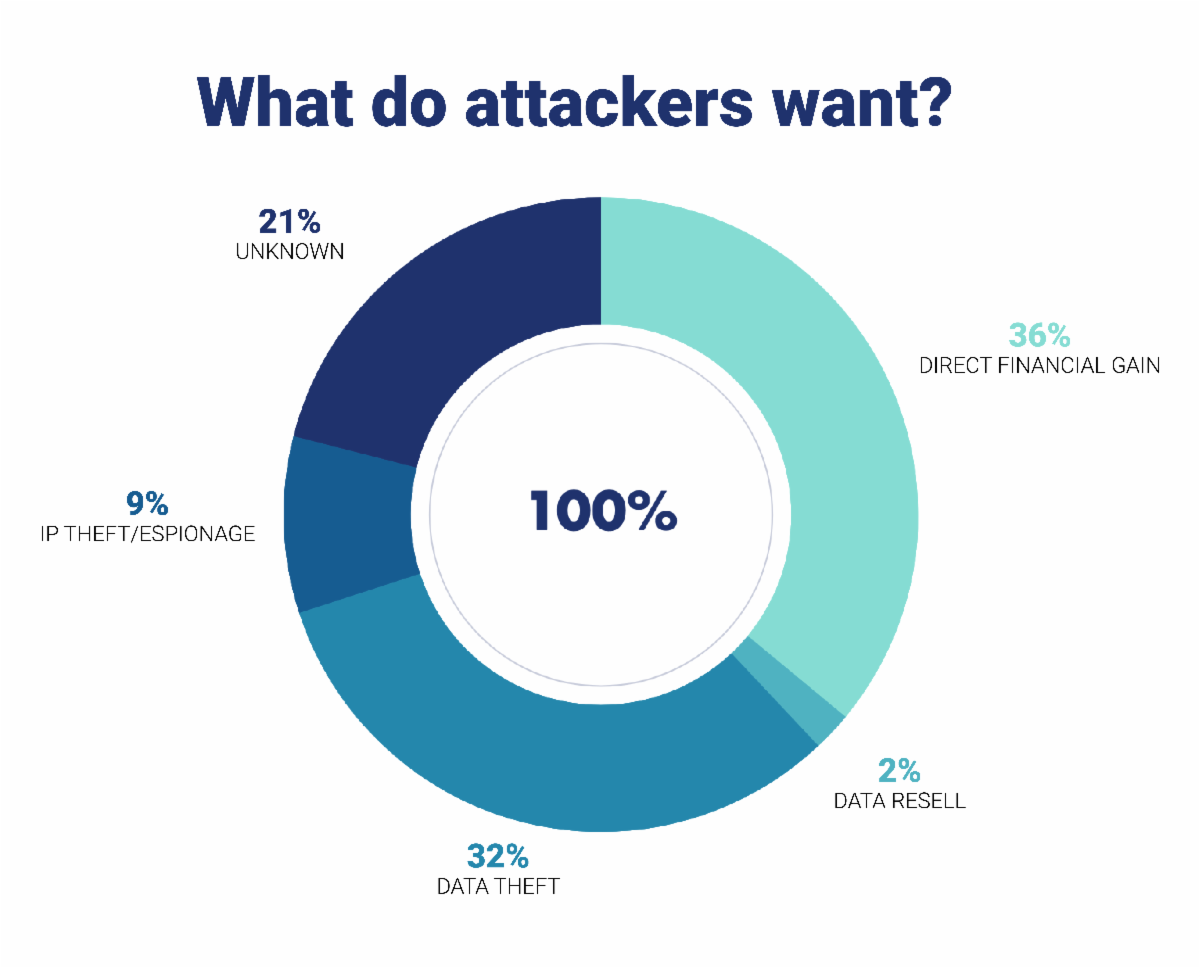
They are after your data, and leaving it unprotected opens up you and your families to problems that are avoidable with the proper security measures in place.
Cybersecurity firm CrowdStrike published a report showing the increased number of interactive attacks.
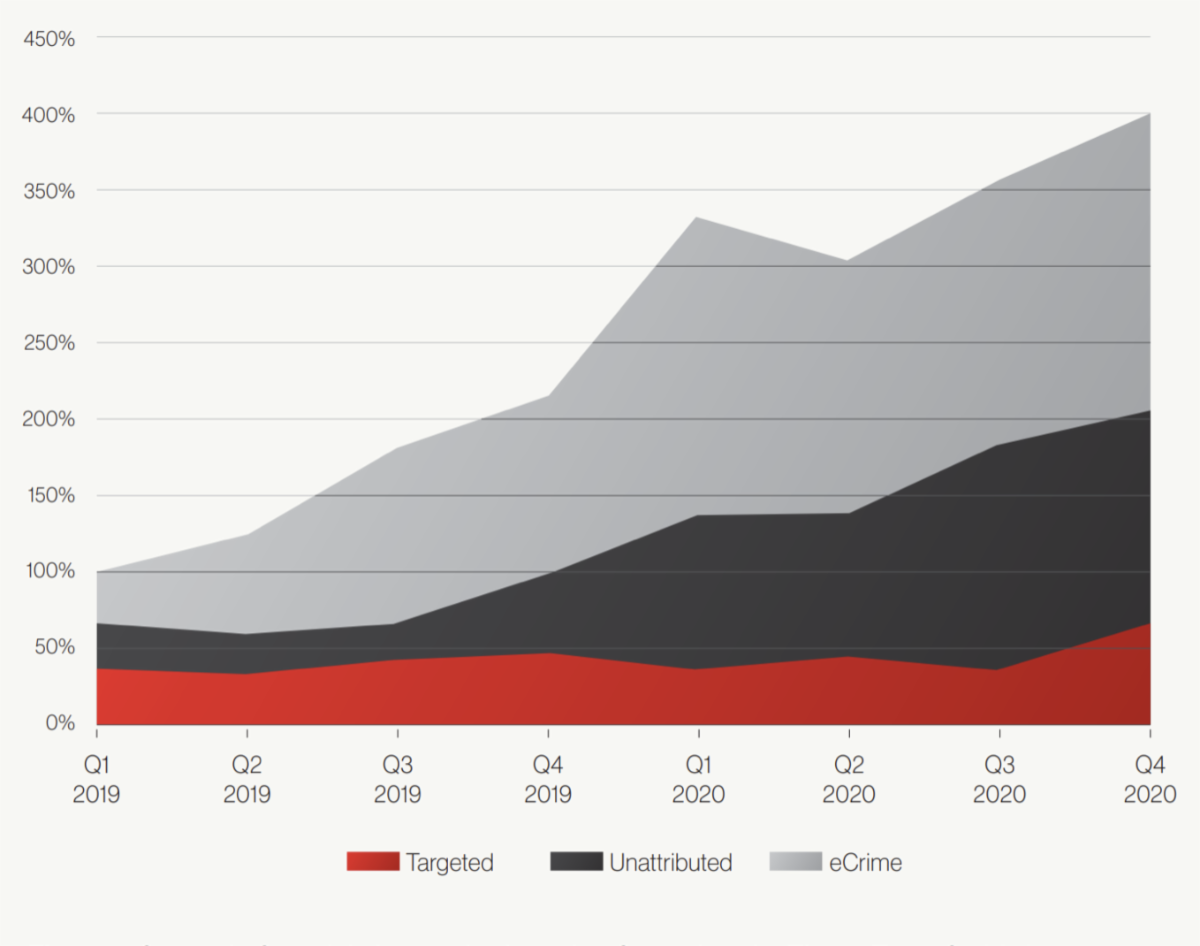
These results are shocking – there has been a fourfold increase in the number of interactive attacks. To that end, we want to re-affirm our commitment to protecting PHI and the data of our Client’s from these attacks:
- ProviderSoft’s infrastructure is hosted on the Microsoft Azure Cloud Platform. Azure is trusted by 95% of the Fortune 500 and boasts compliance with 90+ security and privacy standards, the highest in the industry.
- We received an ‘A’ rating via the Security Scorecard scoring system, which analyzes the security posture of our public facing assets.
- We have Multi-factor authentication enforced for all critical internal systems.
CrowdStrike Intelligence identified the highest number of ransomware-associated data extortion operations this year.

We want to share some necessary measures being implemented to protect our Clients from ransomeware:
- Vulnerability Management – Rapid7: daily scans of infrastructure and workstations for security vulnerabilities.
- Detection and Response – Rapid7: constant monitoring of security and other events on our infrastructure to detect anomalous behavior
- Enhanced Endpoint Security – CrowdStrike: high-grade antivirus software
- Third-party Incident Response Plan Validation Security drills and recovery plan responses
- Third-party Penetration Testing Breach tests, to find holes in the system.
